Threat Simulator: Breach and Attack Simulation
Simulate attacks on your live network, measure and optimize SecOps spend, and continuously test your security posture
|
|
|
Continuosly Validate Your Cyber Defences
Security is never static. New cyber attacks are constantly emerging and misconfigurations are rampant. How do you take control of an ever-changing threat landscape?
The only way is to attack yourself before hackers can.
A SaaS-based breach and attack simulation (BAS) platform, Threat Simulator continuously tests your defenses by simulating attacks across your production network and endpoints. Built on 20+ years of leadership in network security testing, Threat Simulator helps you identify and fix vulnerable gaps in coverage before attackers can exploit them.
A central component of Keysight's Security Operations Suite, Threat Simulator enables you to do all this and more:
- Test security tools against 20,000+ tactics, techniques, and procedures (TTPs), including MITRE ATT&CK.
- Find and fix misconfigurations and gaps.
- Measure network, email, and endpoint security posture.
- Detect and remediate environmental / configuration drift.
- Prevent past incidents and attacks from happening again.
- Save money by maximizing existing security controls and processes before purchasing new tools.
 |
 |
 |
|
Simulate Mitre Attack Techniques |
Test Networks, Endpoints and Email |
Stay Ahead with Zero-Day Updates |
How Threat Simulation Works
Ensure the highest-performing security for your network and applications.
|
|
Threat Simulator never interacts with your production servers or endpoints. Instead, it uses isolated software endpoints across your network to safely exercise your live security defenses. Dark Cloud, our malware and attack simulator, connects to these endpoints to test your security infrastructure by emulating the entire cyber kill chain — phishing, user behavior, malware transmission, infection, command and control, and lateral movement. |
 |
Finding problems is easy. Fixing them is harder. That's why Threat Simulator provides user-friendly, step-by-step instructions to close every security gap our assessments identify. Featuring product-specific recommendations — including guidance and advice to fine-tune and optimize your SIEM tools — our patented remediation engine cuts through clutter to close your most critical security gaps with actionable intelligence. |
 |
Security information and event management (SIEM) tools are the backbone of any security team. But amidst a daily flood of logs, alerts, and notifications, it can be difficult to correlate all that activity with an actual attack. That's why Keysight partners with leading network security tool vendors — including IBM, Splunk, CheckPoint, Cisco, Fortinet, Palo Alto Networks, and Juniper. Threat Simulator makes it easy to pinpoint indicators of compromise (IoCs) and customize SIEM alerts, so you can spend less time dealing with alert fatigue, and more time responding to threats. |
 |
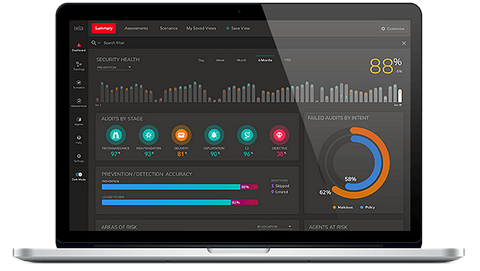
A pure software solution, Threat Simulator simplifies deployment and cost-effectiveness with auto-scaling design and software-as-a-service (SaaS) management. An intuitive dashboard shows you everything at a glance — including security gaps, audit statuses, and security measurements over time — while a user-friendly interface minimizes errors and saves valuable time. |
Tap Into Threat Intelligence, 24/7/365
The world leader in application and security testing, our Application and Threat Intelligence (ATI) Research Center keeps Threat Simulator updated with the latest threats. Our database contains more than 50 million records, and millions of new threats are analyzed and cataloged each month.
With continuous updates from our feed, you'll always be able to emulate the most relevant and active cyber security threats and attacks. But curtailing threats also means knowing your enemy. So, when you need to dive a little deeper, you can drill down on specific attacks to learn even more. From cyber attack signatures to evidence of malicious activity, our database makes it easy to leave no stone unturned.
Dont Just Find Problems. Fix Them.
Knowledge is power. But without action, it's only a piece of the puzzle. Unfortunately, most tools will only help you find problems — they won't help you solve them.
With Threat Simulator, you'll always be a step ahead. Continuous, automated assessments make it easy to identify gaps, while a patented recommendation engine gives you the actionable intelligence you need to close them. Whether you need to deploy a new patch on your NGFW, enable a new functionality on your IPS, or install a new tool altogether, you get product-specific, step-by-step instructions to optimize your architecture and strengthen your cyber security defenses.
Get Quote | Request Demo | Get in Touch